Cyber Warfare & The Civilian Hacker Army
Ukrainian aligned Civilian Hackers caused chaos inside the Russian Federation.
The 2022 full-scale invasion led to some rapid developments in the cyber & information space.
If you aren’t a medium member, you can read with no paywall via substack
If you’ve been watching the developments in Ukraine for more than a few minutes, it won’t take you long to realise how big a role the cyber domain and the radio spectrum have played in a conflict such as this. As such, we’ve seen dramatic shifts in the way cyber and information warfare are pursued. Propaganda has played a large part in this process and it’s no exaggeration to say that that information battleground has been an intense space at times.
More than a few people though, believe that Russian aggression started in 2022 with the full-scale invasion. However the reality is that things started in 2014, and one of the first large-scale non-kinetic shots that accompanied this was an intense cyberattack, aimed at taking Ukrainian power infrastructure offline. Since then, the cyber front has seen ongoing activity, including data breaches, social engineering and phishing attacks and the ever-present Distributed Denial of Service (DDOS) attacks.
The Industrial Control System
The concept of targeting industrial control systems for military gain isn’t exactly a new idea. But pairing these tools with cyber warfare techniques means that adversaries now have new avenues to help disrupt productivity.
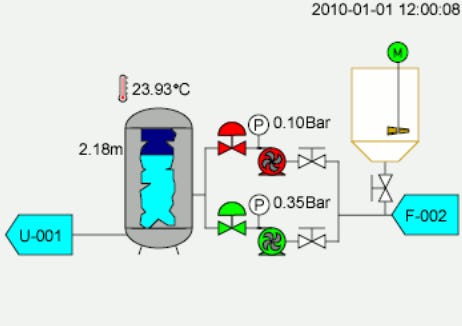
At the heart of these types of systems, is the Industrial Control or Supervisory Control and Data Acquisition (SCADA) system. Effectively an embedded computer system, SCADA systems play a significant role in enabling manufacturing and optimising production.
While this might sound like a slightly vague description one thing that is important to impart is that these systems have worked their way into nearly every facet of modern life. Hospitals, Manufacturing Plants, Utility providers and other essential infrastructures all rely on SCADA-type systems. Further to this, not only do they provide control systems but they also enable remote monitoring and in some instances, even remote updates.
As you’d imagine, when things are great these can be pretty beneficial things to have in the modern world. Unfortunately, though, the depth at which they are integrated with modern systems paired with the age of some systems means that typically, there are cybersecurity issues with this concept as well.
Cybersecurity Issues
When we think about manufacturing technology it’s easy to go back literally decades and consider the ramifications that implementing this technology has. And, one commonly seen but particularly unique probably that’s regularly seen in modern society, is the difference in cybersecurity attitudes over the years.
SCADA systems are somewhat unique due to their long-lasting nature and specialised roles and because of this, it’s entirely normal to find badly secured systems not due to malice, but due to vastly different generational attitudes toward cybersecurity.
In fact, in some older systems, it’s fair to say that cybersecurity wasn’t even a consideration at all, and for many, this wasn’t ever a problem until things got put online. At that point, things like older protocol types and a lack of encryption would start to become greater concerns.
So, in the security world, you’ll see plenty of discussion around SCADA security, including its vulnerabilities and how to modernize and mitigate cybersecurity issues in more modern installations.
On the flip side, many a red team member has initiated an attack via a badly configured or forgotten system.
Relevance in Wartime
For many people, the first real cyberattack on a commercial installation came with the delivery of Stuxnet, which was designed to target centrifuges linked to the Iranian nuclear program. Beyond this though, it’s generally accepted that this was the turning point that would force many countries to consider their options for both offensive and defensive cyber operations.
For Ukraine, this warning would come in 2014 and it’s fair to say that by the time 2022 rolled around, things were much more streamlined. With necessity being the mother of invention though, the full-scale invasion would force this process to become even more refined.
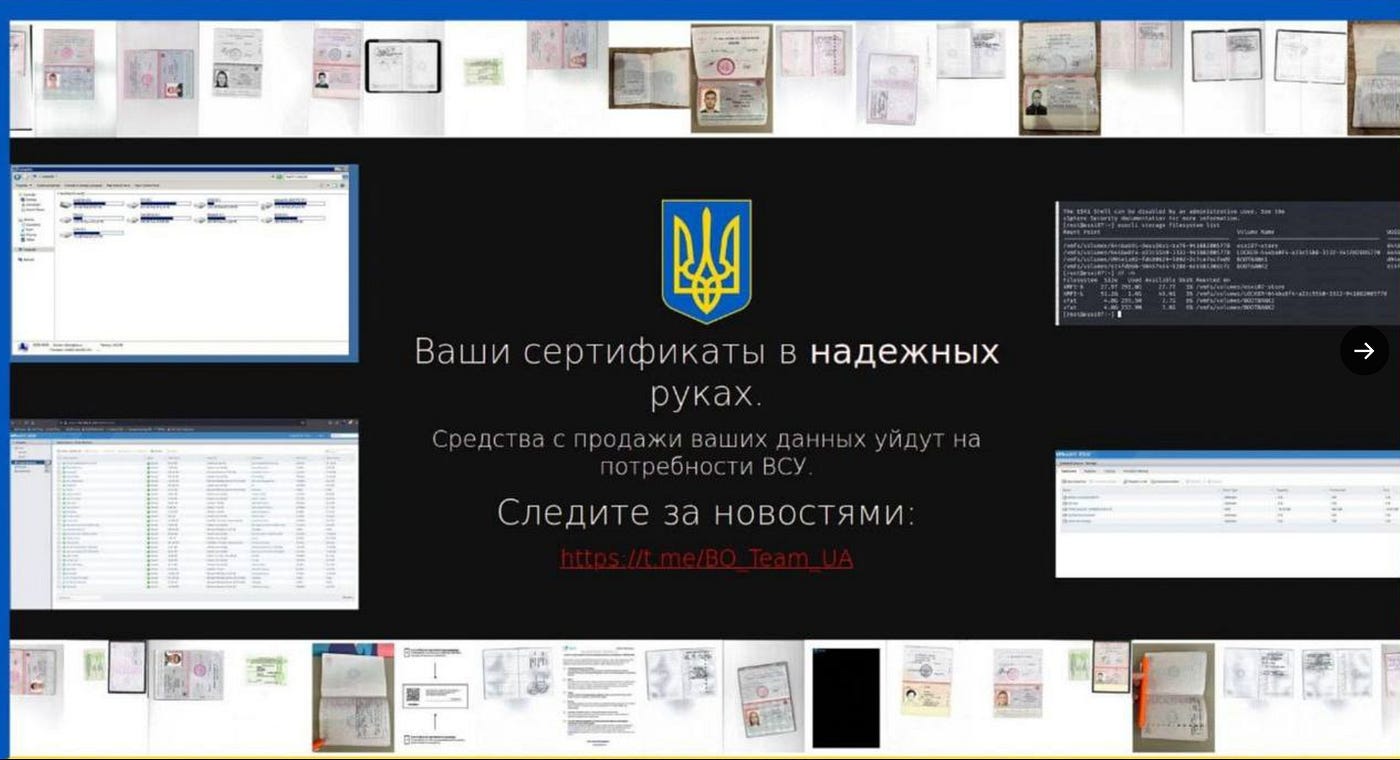
This would take many shapes and one of the most interesting parts of this was the rise of a civilian hacker army helping to work towards a Ukrainian victory. As part of this, civilian hackers the world over came together to help take the fight to the Russians.
One thing that was noticed early, was lax attitudes toward cybersecurity. With many systems being old, or badly configured, good-quality target identification would eventually lead to a large number of vulnerable systems being identified.
Real World Drama
As you’d imagine, vulnerable systems in wartime (with some civillian exceptions) are generally considered legitimate military targets. This means that it didn’t take long for many of these vulnerable systems to be targeted.
In the early days of the war, the DDOS attack was king due to its distributed effects, making it harder to offset the effects of an attack. With the passage of time though, we’d eventually see more complex attacks being launched, intending to do longer-lasting damage.
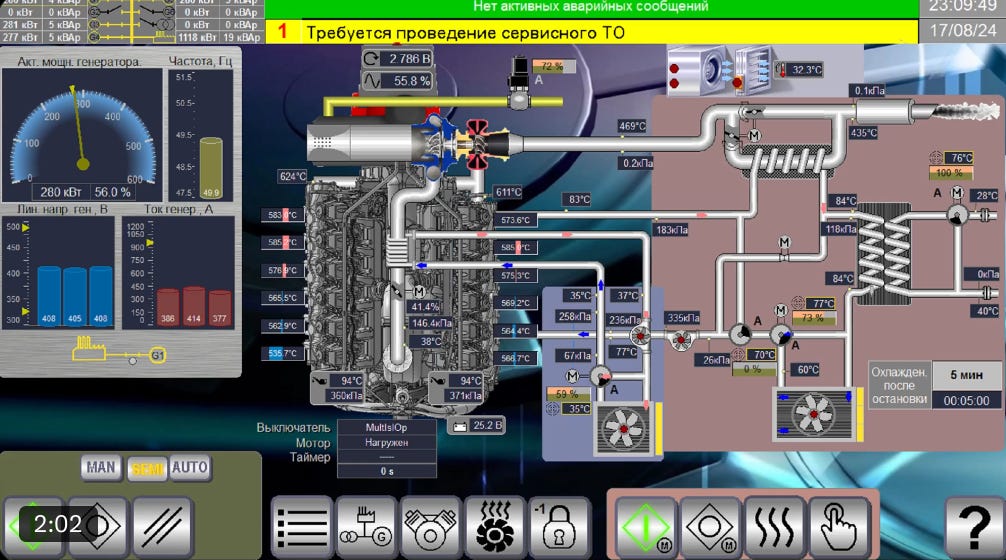
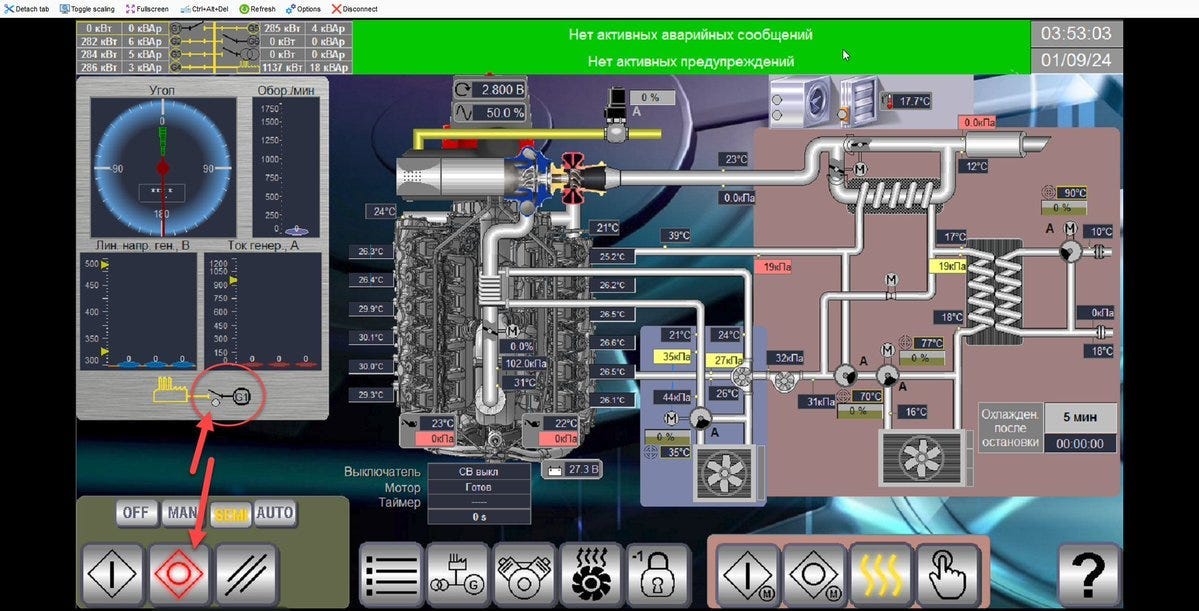
A recent attack that was posted to X / Twitter, would uncover just how far this process has come from the early days of the war. The group responsible for this attack claimed that they were present for months prior to taking it down.
While the location of the system was not revealed, it was disclosed that the target was a power generation facility, located inside Russian territory.
In Closing
One thing that we see in this more modern war, is the sheer volume of footage that is uploaded for both propaganda and historical purposes. With telegram, X and Instagram all being popular places for sharing wartime content, OSINT analysts have a vast array of footage to help establish historical accuracy.
In the earlier days, offensive operations would have been conducted with little in the way of fanfare or promotion. Typically we’d only see more about these types of operations long after they’d ended.
In today's world though, it's not uncommon for footage to be posted online before the dust has settled. Because of this, OSINT analysts have been able to closely track platform movements and losses much more effectively than they have in previous conflicts.
The battle for the information space will continue to rage on, while the frontlines of Ukraine are helping to shape new strategies that more effectively leverage the data-driven techniques that helped shape the modern world.
To support Ukraine in the defense of their homeland, visit the United 24 Website.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
What The Tech?! Rocket Engines
OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates